Well at least he should be according to
Sartre though I am not entirely convinced the repercussions of my choice to manufacture another folding chair were entirely thought through.
After my most recent posting the urge to do "just one more iteration" became too great and I succumbed. I therefore present version 4 of my folding chair which corrects all the previously discovered issues.
The popliteal height (420mm) and buttock popliteal length (400mm) are both comfortable for a wide selection of people. The seat slopes a few degrees front to back and the back rest no longer comes further forward than the rear of the seat.
There is a small gap above where the seat folds in when flat but that is only an aesthetic issue when being stored.
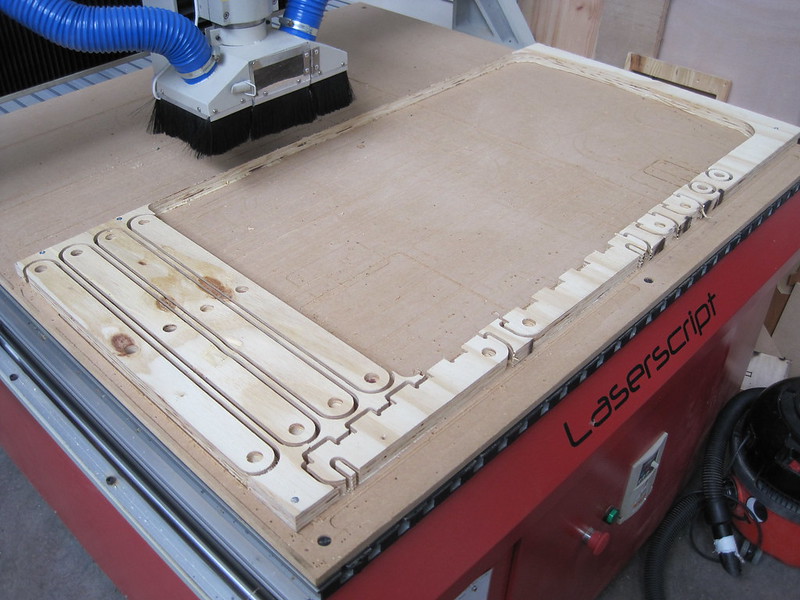
Manufacture wise the design is simple to produce although I really will have to teach our CNC router how to use the
round over bit to reduce the finishing steps as currently that takes longer than the CNC operation.
In future if I make more of these I will use
this design and, once she is less annoyed at me for making another chair, I am going to consult with my wife on adding some cushioning material to the seat and backrest.
And of course that concludes my furniture making for a while...yeah, right!
there have been comments which have complained about my usage of space on sheets and suggested I waste too much material. That is probably true and in my own defence I have not been working with this machine for very long and am not quite used to what I can "get away with" yet.
I was looking at the sheet after removing the last chair design and had a thought, I had not attempted a
side X type folding design and perhaps I could squeeze one into the offcuts? I kinda got carried away, it roughly went:
- Measure the available offcut space
- Measured the remaining 18mm dowel leftover from my dowel hinge experiments
- Found the largest width and height area I could get out of the sheet the CNC router ruined.
- Sketched a design
- Capture design to a DXF
- Carefully spread the pieces over the available material in the CAM software
- Generate a toolpath.
- Cut material
If all of that sounds like and utterly mad way to design a size X stool, you are of course correct, but it worked, and it was a very fast process taking less than four hours from idea to stool.
There are a couple of issues:
- the popliteal height is 470mm ( I was aiming at 420 and missed...badly)
- It uses a lot of expensive hardwood dowel (1373mm plus cutting width and only way I could get it accurate was to use the disc sander to remove fractions till the length was correct)
- I used pockets for the interference seat joints rather than through cuts and discovered that you need to allow tolerance depth (the pegs are 10mm deep and the sockets need to be at least 10.2 not the 10mm I cut)
- Dowel joints are great but have a small surface area so friction fit joints work loose.
The seat went together dry fit and Paul tested it for me, however that last issue soon made me realise that this time I was going to have to resort to glue. Yes, sorry, this design needs to be glued to remain stable (I know plywood contains glue...please stop telling me that).
It is pretty simple to put together and aside from needing half the clamps in makespace to hold it in place while the glue dried, I had no trouble.
Though this is definitely not a case of use glue "sparingly" I put generous amounts in all the dowel joints and all the seat slots and got very little ooze so I guess it could have used more.
The final varnished stool is pretty robust but folds up nicely the concept of hooking to its own pivot dowel means it stays closed when flat which makes it very portable.
Total cost was an estimated 10.00 ( 4.25 dowel, 2.50 of 24mm ply, 1.75 for 18mm ply, 0.50 tool wear, 1.00 varnish) though the materials in my case could be argued to have cost nothing.
It has been suggested that I could make an entire picnic table and chairs set this way but if I did I would reduce the stool height by 50mm and examine ways to use less dowel.
This is usually the bit where I point you all at the freely usable
design files on github and
all the photos on flikr and wrap up.
But you know what the Monty Python boys say? "
Nobody Expects the Spanish inquisition"
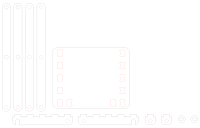
Or in this case my final (and yes I am going to do something else next) chair design. It is based on the stool, in fact it is the stool design with the outer legs extended and a back rest added.
The modified design reduces the dowel requirements to 775mm but requires a bit more sheet material (cannot get this one entirely from offcuts).
Total cost was an estimated 10.50 ( 2.50 dowel, 4.50 of 24mm ply, 1.75 for 18mm ply, 0.50 tool wear, 1.25 varnish).
Because it is based on the stool design it suffers from the height issue and in addition the back rest is a bit far back to be completely comfortable.
Neither of the side X designs have flaws that interest me enough to follow the iterative approach again to solve them. Both the designs work well enough and rounded out my adventures with folding chairs and indeed furniture for now.
As always the design files are on
github and the
images are on flikr.









 After one week of campaign on -vote@, many subjects have been mentioned already. I m trying here to list the concrete, actionable ideas I found interesting (does not necessarily mean that I agree with all of them) and that may be worth further discussion at a less busy time. There s obviously some amount of subjectivity in such a list, and I m also slightly biased ;) . Feel free to point to missing ideas or references (when an idea appeared in several emails, I ve generally tried to use the first reference).
On the campaign itself, and having general discussions inside Debian:
After one week of campaign on -vote@, many subjects have been mentioned already. I m trying here to list the concrete, actionable ideas I found interesting (does not necessarily mean that I agree with all of them) and that may be worth further discussion at a less busy time. There s obviously some amount of subjectivity in such a list, and I m also slightly biased ;) . Feel free to point to missing ideas or references (when an idea appeared in several emails, I ve generally tried to use the first reference).
On the campaign itself, and having general discussions inside Debian:


 I am transitioning my
I am transitioning my  I started by explaining why having root access to your system is really important, including
I started by explaining why having root access to your system is really important, including 



 The Google Maps client comes with every Android system, the above shows the location of the LUV meeting.
The Google Maps client comes with every Android system, the above shows the location of the LUV meeting.


































 Dear friends of Debian,
Dear friends of Debian, I've spent chunks of the last couple of days fighting a problem that's existed for about 25 years. The 8086 was a 16-bit processor with a 20-bit address space, limiting the maximum physical address that could be accessed to 1MB. However, quirks of the segmented memory system meant that addresses greater than 1MB could be constructed - these would wrap around to the bottom of memory. Because loading the segment registers was a time consuming operation, some programmers used this behaviour as a performance optimisation.
I've spent chunks of the last couple of days fighting a problem that's existed for about 25 years. The 8086 was a 16-bit processor with a 20-bit address space, limiting the maximum physical address that could be accessed to 1MB. However, quirks of the segmented memory system meant that addresses greater than 1MB could be constructed - these would wrap around to the bottom of memory. Because loading the segment registers was a time consuming operation, some programmers used this behaviour as a performance optimisation. Ok, so following the trend, I created some time ago a new GPG
key, which I'm now transitioning too. I've set up a transition
document, available at
Ok, so following the trend, I created some time ago a new GPG
key, which I'm now transitioning too. I've set up a transition
document, available at  -----BEGIN
-----BEGIN